

EV Charging Stations Cyber Vulnerabilities Could Be EVs Achilles Heel
Electric vehicles (EVs) are a critical pillar of the global automotive revolution we’re experiencing today. Over the next five years, the US government will invest $5 billion in charging infrastructure, paving the way for long-distance travel, V2X, and V2G, along with more sustainable transportation.
As the number of EVs continue to rise, so have concerns over range, reliability and security of charging points. Boosting trust in the charging infrastructure is critical to providing a solid customer experience and accelerating EV adoption.
Upstream’s research team constantly analyzes automotive and smart mobility-related cybersecurity incidents to provide critical information to our customers and community, while making sure that our technology remains one step ahead of hackers and fraudsters.
In our analysis of 100+ publicly reported automotive cyber-related incidents since the beginning of 2022, EV charging has been identified as the number one emerging attack vector.
Charging stations’ growing number of reported security vulnerabilities could be EV’s Achilles heel. It is imperative to understand how hackers and researchers exploit these vulnerabilities and how you can secure vehicles and mobility applications to mitigate future attacks.
EV chargers are vulnerable to physical and remote manipulation
OEMs and charging stakeholders must rely on a complex and multi-layered charging infrastructure to ensure convenient and affordable public chargers are available to power EVs and eliminate range anxiety and adoption barriers.
As EV charging communication protocols evolve, valuable personal data is transferred both ways using physical and wireless connections, including location, behavior, Personally Identifying Information (PII) and billing details.
However, most EV charging stakeholders are still in the early stages of implementing advanced cybersecurity platforms, and are not yet required to follow regulations and standards similar to UNECE WP.29 R155 and ISO/SAE 21434.
The EV gold rush has resulted in severe security flaws in charging infrastructure — exposing EV users to fraud and ransomware attacks, and making chargers vulnerable to physical and remote manipulation that slows them down or stops their functionality altogether.
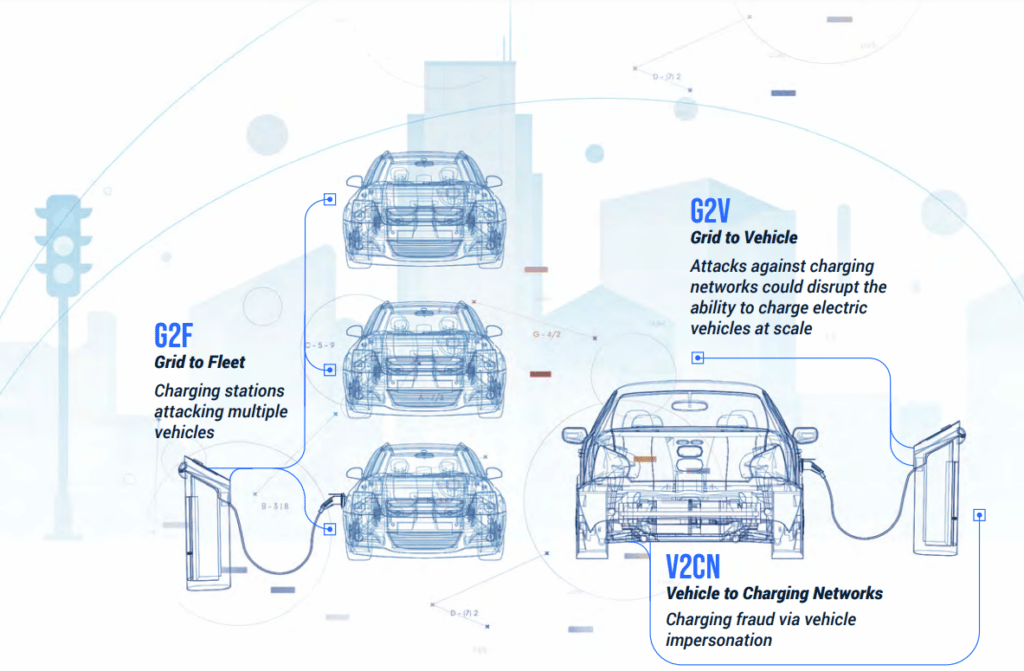
Furthermore, OEMs and various charging infrastructure stakeholders must mitigate additional risks to EVs across a variety of charging attack vectors:
- Vehicle to Charging Networks — charging fraud via vehicle impersonation
- Grid to Vehicle — attacks against charging networks could disrupt the ability to charge electric vehicles at scale
- Grid to Fleet — charging stations attacking multiple vehicles
Here are a few EV charging vulnerabilities that have made headlines in the first half of 2022:
- January 2022
Seven vulnerabilities were found in multiple charging stations which allowed remote attackers to impersonate charging station admin users and carry out actions on their behalf. - February 2022
Russian electric vehicle chargers were hacked and disabled by a Ukrainian EV charging parts supplier as part of a cyberwar effort. - April 2022
New Combined Charging Stations (CCS) attack technique found with the potential to disrupt the ability to charge electric vehicles at scale. - April 2022
An EV charging station in the Isle of Wight was hacked to show inappropriate content, with some EV owners also experiencing high voltage fault codes, leaving them stranded. - May 2022
Rise in hacks of EV charging stations including ransomware attacks against chargers and EV users. - May 2022
Rise in black-hat cyber criminals targeting EV charging stations to make money illegally, surpassing white-hat hackers working with stakeholders.
To learn more about EV charging infrastructure incidents and vulnerabilities, checkout Upstream’s AutoThreat® intelligence repository
Protect EVs and charging stations with managed VSOCs
Attacks on charging stations reveal more endemic problems to the EV ecosystem, where being first to market often overrides sound security practices. They have become increasingly nefarious as transportation becomes increasingly electrified. Consumer adoption of EVs, as well as the electrification of vehicle fleets, can be profoundly affected by these risks.
The success of electric vehicles depends on a reliable, consistent network of charging stations. OEMs, charging networks and smart mobility stakeholders need to enforce a new cybersecurity paradigm that makes sure consumers can trust the charging infrastructure they use and that EVs are protected at all times.
Upstream’s cybersecurity platform and managed vSOC were designed to ensure OEM’s and charging infrastructure stakeholders can deliver holistic protection against cyber threats. Based on digital twins of vehicles, applications and consumers, Upstream layers automotive and cyber expertise to monitor and secure charging infrastructure from cybersecurity vulnerabilities, attacks, misconfigurations, and design flaws.

