Upstream
API Security
Secure operational APIs from cybersecurity attacks and vulnerabilities to mitigate data breaches and operational disruptions in near real-time.
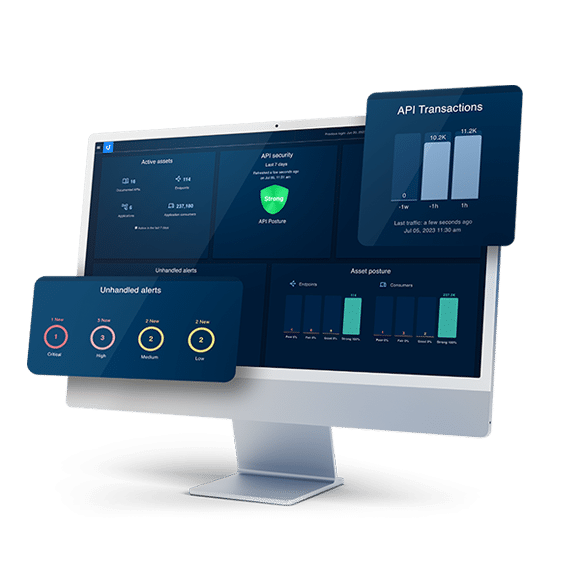
The most extensive API Security coverage
Purpose-built to protect business operations, applications and services
OWASP Top Ten
Comprehensive detection of OWASP API Security Top Ten 2023 and 2019 risks for coverage against the most common API threats and attacks.
Business Logic
Dedicated pre-defined detection of business-logic anomalies alongside detectors created using the no-code platform for specific use cases.
Fusion & Contextual
Effective detection of unknown threats and attacks utilizing advanced AI/ML models to recognize complex low and slow attacks.
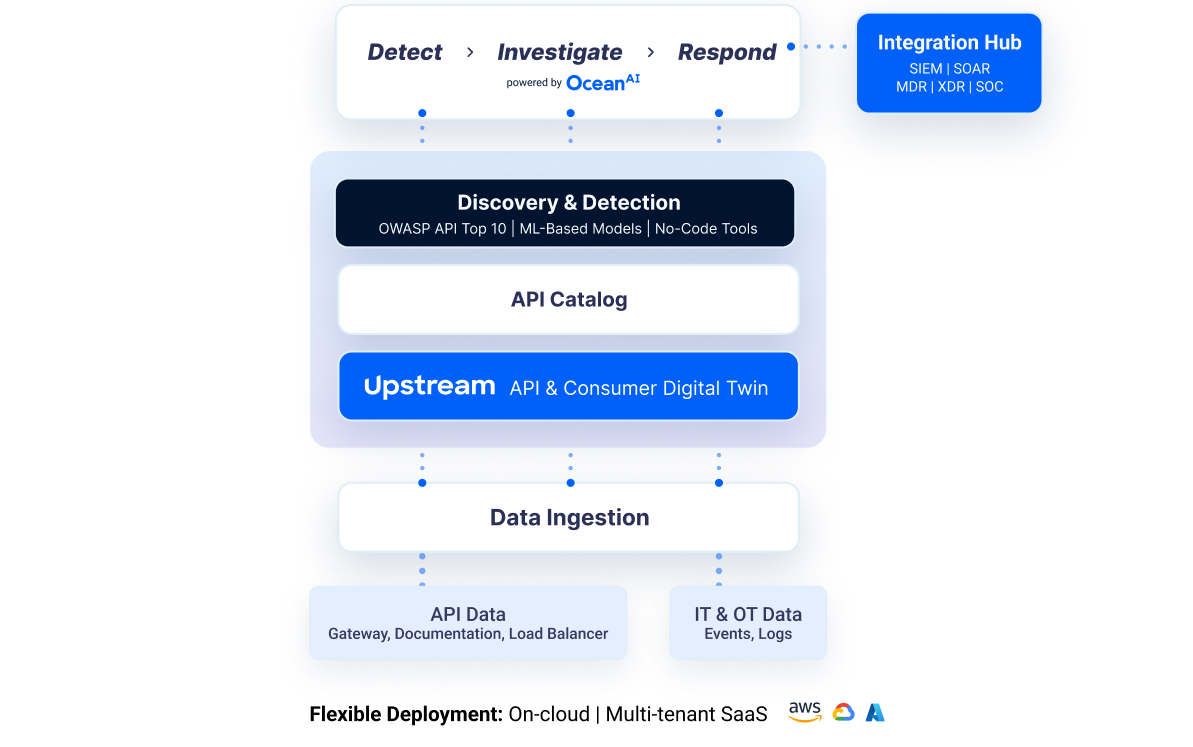
Deep Contextual Detection of API Traffic
Alongside Operational Data Feeds
-
Leader in API & Cloud Security
Upstream actively monitors billions of API transactions a month, alongside millions of assets and endpoints for global Fortune 500 companies. Upstream is a recognized leader in API and cloud cybersecurity with customers including leading OEMs, automotive suppliers, and mobility service provider.
-
Purpose-Built for Business Continuity
Ensure operations run with no disruptions with near real time detections that enables application developers to safely deploy and monitor APIs and risks, supporting fast time-to-market. Upstream leverages deep domain expertise in a wide range of industries to provide pre-built detection capabilities that identify business logic anomalies and API misuse.
-
Fusion Detection
Gain a contextual understanding of the impact API transactions by correlating additional organizational and operational data feeds from IT, IoT, OT systems. This unique correlation offers deep contextual analysis of the business logic and enables enhanced API-related detection and mitigation.
-
Deploy Anywhere
Designed for flexibility, Upstream API Security can be deployed in any environment (on-cloud, on-prem, etc.) or as multi-tenant SaaS. Reduce cloud costs while ensuring data privacy, PII protection, and regulatory compliance by keeping your data in your existing environments.
-
GenAI-Powered Investigations
The Upstream Platform leverages Ocean AI, an integral advanced Gen-AI layer, enabling cybersecurity analysts and SOC teams to investigate cyber risks and extract insights through a simple conversational interface. With these newly introduced GenAI capabilities, cyber teams can optimize alert filtering, handling, and prioritization; they can make smarter, more informed decisions, identify patterns and trends and ultimately accelerate time-to-response.
-
No-Code Platform
Optimize and customize API Security for specific use cases with a no-code detector builder that makes it easy to refine and define anomaly detection to your unique requirements, business use-cases and logic.
-
Designed for Hyperscale
Support API-based applications and services at scale, with massive volumes of API transactions. Upstream API Security is purpose built to support the ingestion and normalization of massive amounts of data generated by operational and organizational systems alongside growing API transaction volumes.
Based on a robust digital twin of both operational assets and API consumers as well as a pre-defined suite of business logic and cybersecurity anomaly detectors, the platform protects against API misuse and manipulations in near real-time. With the rise of complex low and slow attacks, the platform is uniquely positioned to deliver comprehensive detection and investigation of sophisticated attacks over time.
Discover
Get a complete catalog of all your APIs, with automatic inventorying of real-time live traffic, as well as documentation sources (e.g. Swagger). Deliver comprehensive discovery of all documented, shadow, and zombie APIs as well as those used by 3rd party, organizational or internal services.
Detect
Detect a wide range of API-based cyber attacks in near real-time. Utilize the only solution that correlates between the attacked API, the contextual implications, and the impact on applications and consumers. With coverage of the known vulnerabilities in the OWASP API Security Top Ten alongside unknown threats and attacks detected by proprietary machine learning algorithms and no-code detectors.
Monitor
Strengthen your security posture with continuous discovery of static and dynamic traffic sources for ongoing conformance analysis. Identify potential vulnerabilities in your API landscape introduced by updates or additional developments, ensuring continued operations with no disruption or downtime.
Mitigate
Leverage existing organizational workflows, or build new ones, and tools to automatically push alerts relating to API vulnerabilities and threats. Empower security teams to effectively investigate, respond and mitigate cyber threats and developer misconfigurations.

