Resources

- Cybersecurity
- Regulatory Compliance
- Threat Intelligence
Upstream’s H1 2023 Automotive Cyber Trend Report
This report focuses on the 1st half of 2023 and sheds light on key trends and emerging cybersecurity threats that…
Research Reports

- Cybersecurity
- Regulatory Compliance
- Threat Intelligence
Infographic: The Automotive Cybersecurity Inflection Point 2024 Report
The Automotive industry is rapidly expanding into a vast smart mobility ecosystem, introducing new levels of cyber sophistication and attack…

- Cybersecurity
- Regulatory Compliance
- Threat Intelligence
2024 グローバル自動車サイバーセキュリティレポートUpstreamのグローバル自動車
サイバーセキュリティレポートは、自動車サイバーセキュリティの状況に関する包括的な概要を提供します。Upstreamの研究者が数百件の自動車サイバーインシデント(過去10年間で1468件、2023年だけで295件)を分析し、数年先に渡る実用的なインサイトと予測を提供します。

- Cybersecurity
- Regulatory Compliance
- Threat Intelligence
Global Automotive Cybersecurity Report 2024
The Automotive industry is rapidly expanding into a vast smart mobility ecosystem, introducing new levels of cyber sophistication and attack…

- Cybersecurity
- Regulatory Compliance
- Threat Intelligence
Upstream’s H1 2023 Automotive Cyber Trend Report
This report focuses on the 1st half of 2023 and sheds light on key trends and emerging cybersecurity threats that…

- Cybersecurity
- Regulatory Compliance
- Threat Intelligence
Global Automotive Cybersecurity Report 2023
The Automotive industry is rapidly expanding into a vast smart mobility ecosystem, introducing new levels of cyber sophistication and attack…
White Papers
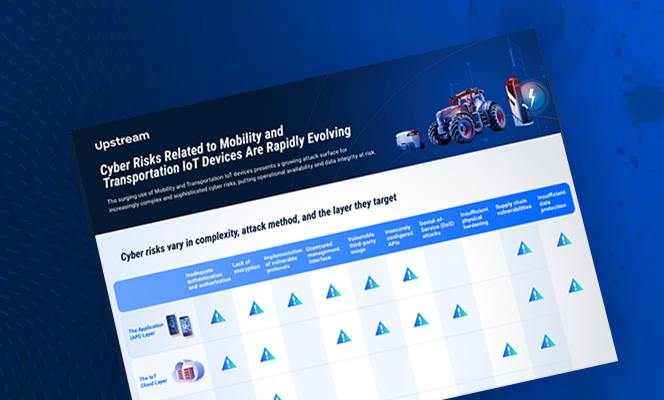
Cybersecurity Challenges in the IoT Device Landscape

- Cybersecurity
- Regulatory Compliance
Navigating the Complex Landscape of Automotive Cybersecurity Regulations
Generative AI (GenAI) is reshaping the automotive industry, offering personalized experiences and enhanced safety, but also introducing risks around inaccurate…

- Cybersecurity
EV 充電所 拡大に向けて: EV充電所インフラ安全確保への課題
Delivering driver confidence with robust charging networks has created new opportunities for hackers to penetrate OEM and Tier-1 networks by…

- Cybersecurity
Leading the Charge: Securing Charging Station Infrastructures
Delivering driver confidence with robust charging networks has created new opportunities for hackers to penetrate OEM and Tier-1 networks by…

- Cybersecurity
Protecting Electric Vehicles: Modern Cybersecurity Solutions and the Road to Revenue
There is much to enjoy in the performance of electric vehicles and advanced features of electric vehicles, yet each connected…
Webinars

- Cybersecurity
Switched on: leveraging cyber resilience to safeguard the future of EVs
The mobility ecosystem has identified a clear priority in accelerating the adoption of electric vehicles (EVs). However, as the proliferation…

- Cybersecurity
Scaling Software-Defined Vehicle Security, without Increasing Costs
Connected and software-defined vehicles generate vast amounts of data – upwards of 25 GB an hour per car. To help…

- API Security
- Cybersecurity
- Threat Intelligence
- Vehicle SOC
The automotive cybersecurity inflection point in 2024: from experimental to massive-scale attacks
Upstream’s definitive 2024 Global Automotive Cyber Trends Report is coming out this month. Join us for this 40-minute session as…

- Cybersecurity
- Vehicle SOC
Live from the vSOC: gearing up towards 2024
Upstream’s cybersecurity experts discuss the crucial role of the vehicle security operations center (vSOC), giving a behind-the-scenes tour of vSOC…

- Cybersecurity
ABeam & Upstream webinar: Emerging cybersecurity risks in automotive, manufacturing & smart mobility
The introduction of connected and Software Defined Vehicles is introducing many digital and business opportunities. Yet at the same time…
Compliance Q&A

- Cybersecurity
- Regulatory Compliance
Relationship | ISO/SAE 21434 and WP.29 CSMS
The WP.29 regulation and the ISO/SAE standard are complementary and both look at securing modern vehicles in a similar way.…

- Cybersecurity
- Regulatory Compliance
OEM Compliance | ISO/SAE 21434 and WP.29 CSMS
Upstream Security provides an end-to-end solution for post-production monitoring as required by both the WP.29 regulation and the ISO/SAE standard. This is done using two cybersecurity…

- Cybersecurity
- Regulatory Compliance
Supply Chain Strategies | ISO/SAE 21434 and WP.29 CSMS
There are multiple possible strategies to secure the supply chain. And securing the supply chain is mandated both by the WP.29 regulation and by…

- Cybersecurity
- Regulatory Compliance
Cloud-Based Automotive Cybersecurity | ISO/SAE 21434 and WP.29 CSMS
The benefit of a cloud-based cybersecurity solution is that it’s able to secure the three primary elements of a connected vehicle. The first element…

- Cybersecurity
- Regulatory Compliance
The Challenges | ISO/SAE 21434 and WP.29 CSMS
There are four major challenges in securing connected vehicles. All of these challenges are addressed by the WP.29 regulation and the ISO/SAE 21434 standard.…

- Cybersecurity
- Regulatory Compliance
Cybersecurity Throughout Vehicle Lifecycle | ISO/SAE 21434 and WP.29 CSMS
Ensuring vehicle cybersecurity across its lifecycle is required both by the WP.29 regulation and by the ISO/SAE standard. And doing that is actually a challenging…
Videos

- API Security
Embracing Next-Gen API Security with Upstream
Upstream has introduced the next-generation solution for API Security, purpose-built for the transportation and mobility ecosystem.

- API Security
Meet the Expert: Updates to OWASP API Security Top 10
Michael Kan-Tor from Upstream Research covers the recent updates to the OWASP API Security Top Ten risks. Reviewing all ten…

- API Security
- Cybersecurity
- Threat Intelligence
Meet the Expert: Securing APIs in the Smart Mobility Ecosystem
Daniel Blum, Product Manager at Upstream Security, discusses how context and an understanding of the automotive and smart mobility use-case…

- Cybersecurity
Meet the Expert: Enhancing SIEM Solutions for Vehicle Cybersecurity
Learn how Upstream enhances SIEM solutions by adding purpose-built detection and response capabilities for vehicle cybersecurity. Discover the benefit of…

- Cybersecurity
- Threat Intelligence
Meet the Expert: Enhancing Investigations with AutoThreat®
Daniel Blum, Product Manager at Upstream Security, shows the integration between AutoThreat® and the Upstream Platform and how this connection…
TechTalks

- Cybersecurity
- Vehicle SOC
TCS & Upstream: Ensuring and Maintaining Data Privacy in VSOCs
TCS & Upstream discuss about the challenges around connected vehicles data in vSOC.

- Cybersecurity
- Vehicle SOC
Wipro & Upstream Combining vSOC Cybersecurity Expertise
Wipro & Upstream discuss how OEMs and stakeholders can oblige to emerging regulations and cybersecurity challenges as an outcome of…

- Cybersecurity
- Regulatory Compliance
- Vehicle SOC
Upstream & Capgemini Discuss Approaches to Monitoring the Connected Vehicle
In this “Tech Talk” video series, Upstream Security hosts diverse partners who are all top industry leaders and experts to…

- Cybersecurity
- Regulatory Compliance
Upstream & SBD Discuss Regulatory Tips for Tier-1 and 2 Suppliers
Transcript – Hi Jeffrey and welcome to Upstream’s Tech Talk Series. I’m Fay from Upstream Security, which offers a first…

- Cybersecurity
- Regulatory Compliance
Upstream & Deloitte Discuss OEM Opportunities and Obstacles Due to WP.29
Transcript – Hi, Andy and welcome to Upstream’s tech talk series. I’m Fay from Upstream Security and we offer the…

- Cybersecurity
- Regulatory Compliance
Upstream & TCS Discuss Complexities of Cybersecurity Assurance
Transcript – Hi, Sundeep and welcome to Upstream’s Tech Talk series. I’m Fay from Upstream Security and we offer the…
Solution Briefs

Secure Connected IoT Devices in the Mobility & Transportation Ecosystem

- Cybersecurity
The Upstream Platform
Monitor, secure, optimize, and enhance connected vehicles, fleets, and applications with a purpose-built, cloud-based data platform.

- Cybersecurity
Automotive Cybersecurity Data Sheet
Monitor and secure connected and software-defined vehicles with a multi-layer AI-based detection and response (V-XDR) solution

- Fraud
Automotive Fraud Management Product Sheet
Monitor and detect fraudulent activities targeted to bypass subscription fees, gain access to premium features, and manipulate vehicles for warranty-related…

- API Security
API Security for Fleet Management Platforms
Upstream’s API Security Is Purpose-Built to Protect Business Operations, Applications and Services
Case Studies

Canopy Selects Upstream to Safeguard Its Advanced Vehicle IoT Security Systems

Marelli Selects Upstream’s AutoThreat® PRO Cyber Threat Intelligence Solution

Ford Trucks Collaborates with Upstream Security to Protect Its Connected Vehicles Against Cybersecurity Risks

Global commercial vehicle OEM ensures UNECE WP.29 R155 compliance with Upstream
Use Cases

Upstream Detects a Critical Vulnerability in Linux-Based Head Units
Read about how Upstream’s AutoThreat® Intelligence team works to hunt threats that are hiding in the surface, deep, and dark…

Protecting Against Telematics Servers’ Attacks
Use Case

Protecting Against Keyless Entry Attacks
Use Case

Protecting Against Security Threats on Car Sharing Services
Use Case

Protecting Against Remote Multi-Vehicle Attacks
Use Case
Chalk Talks

Upstream’s Cybersecurity Engines
[Transcript] At the core of our Upstream C4 platform we have four cybersecurity engines that work together to protect your…
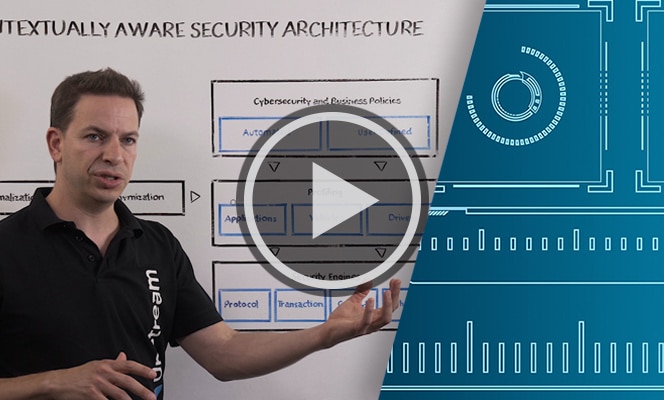
Upstream’s Contextually Aware Security Architecture
[Transcript] In this video, we’re going to talk about the architecture that we use in the Upstream C4 Platform to…
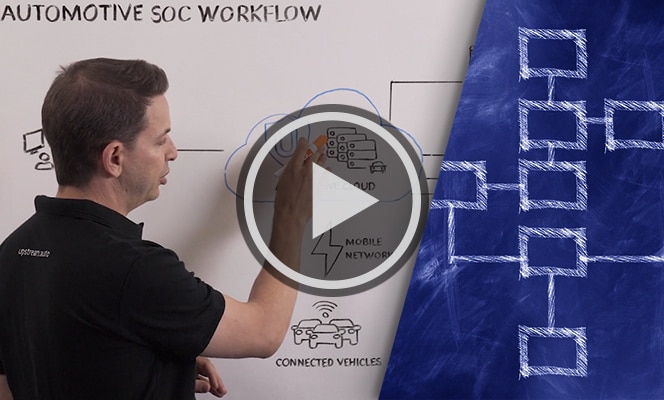
How to Leverage Upstream Platform in a SOC
[Transcript] One of the key groups that use The Upstream platform within the customer environment, is a security team within…

- Cybersecurity
- Regulatory Compliance
Advantages of Upstream’s Cloud-Based Automotive Cybersecurity
[Transcript] Upstream’s value proposition centers around our ability to protect connected vehicles, both OEMs and fleets, from remote cyber attacks.…

Upstream’s Centralized Connected Car Cybersecurity Platform
[Transcript] When we looked at the problem of how to secure a connected car, we had three goals in mind…
Podcasts

- Cybersecurity
Autoline: Cybersecurity Is A Bigger Problem Than You Realize
Is cyber security a big problem in the auto industry? More than you realize. In this episode of Autoline After…

- Cybersecurity
Cybersecurity for Transportation
Transport Topics’ Dan Ronan hosted Upstream’s CEO Yoav Levy to discuss transportation security from a cyber aspect. Some key takeaways: In a world of…

- Cybersecurity
- EV Charging Infrastructure
- Threat Intelligence
AutomotiveNews Turns the Spotlight on Cybersecurity
Upstream Security’s marketing vice president evaluates the automaker’s commitment to fighting cybersecurity threats and the double-edged sword of connectivity. White-hat…

- Cybersecurity
- Threat Intelligence
Automotive cybersecurity: A pre-requisite for connected and software-defined vehicles
The automotive industry is increasingly adopting mobility and cloud technologies, which enable seamless on-the-go experiences such as improved navigation, connectivity,…

Upstream Security Automotive Cybersecurity Report 2019- AudioBook
AudioBook
e-Books
Japanese

- Cybersecurity
- Threat Intelligence
- Vehicle SOC
2024 グローバル自動車サイバーセキュリティレポートUpstreamのグローバル自動車
サイバーセキュリティレポートは、自動車サイバーセキュリティの状況に関する包括的な概要を提供します。Upstreamの研究者が数百件の自動車サイバーインシデント(過去10年間で1468件、2023年だけで295件)を分析し、数年先に渡る実用的なインサイトと予測を提供します。

Upstream Platform – Demo (JP)

- Cybersecurity
- Threat Intelligence
- Vehicle SOC
車両やフリートをサイバーセキュリティ攻撃やリスクから保護
この 40 分間の無料ウェビナーでは、OEM・Tier-1・および商用フリートが、サイバー攻撃によって車両の安全性・顧客の信頼・ビジネス継続性が影響を受ける前に、自社の車両フリートをどのように保護できるかについて、Upstream の専門家が話します。

- Cybersecurity
- Regulatory Compliance
- Threat Intelligence
Upstream 2023 グローバルモビリティ サイバーセキュリティ報告書
弊社のサイバーセキュリティ研究者とアナリストは、2010年の時点で1,173件以上のインシデントを調査しており、それ以来、何百ものディープウェブやダークウェブのフォーラムを監視し、この包括的で実用的なレポートを作成しました。

- Cybersecurity
スマート・モビリティにおけるAPIの保護
UpstreamのAPIセキュリティおよび監視ソリューションは、自動車とサイバーの専門知識とコネクテッドカーの運転状態を階層化して、脆弱性、攻撃、構成ミス、設計上の欠陥からスマート・モビリティで使用されるAPIを保護します。Upstream独自のデジタルツインを使用してAPIを保護、監視する方法の詳細については、ここをクリックしてください。


