Gain unparalleled visibility into the mobility threat landscape with actionable asset-specific intelligence
Book Consultation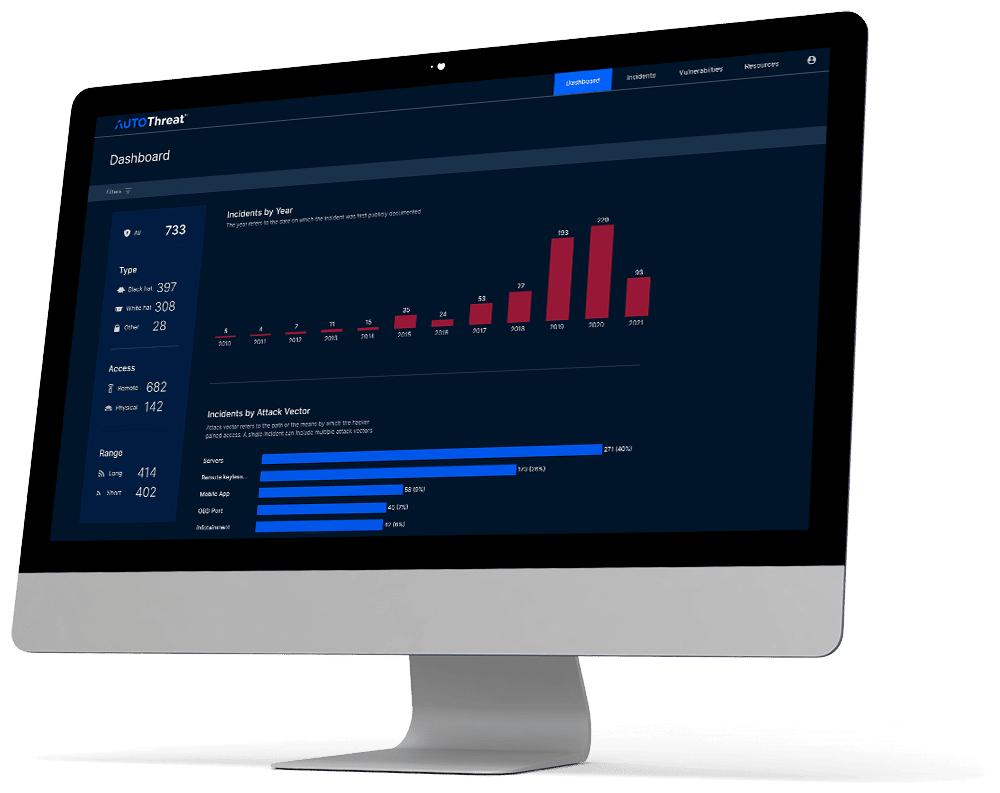
Mobility Cyber
Threat Intelligence
Upstream's AutoThreat® PRO Cyber Threat Intelligence (CTI) offers a comprehensive view of the mobility threat landscape, delivering findings and recommendations based on mobility specific resources to leading global OEMs and smart mobility stakeholders.
Proactively Address Emerging Threats with Deep & Dark Web Intelligence

Cyber Threat Intelligence
Developed specifically for mobility and automotive, AutoThreat® PRO equips stakeholders with visibility, intelligence, and recommendations to deeply understand threat actors' motivations, strategies, and activities targeting their assets, products, and the wider mobility industry.
With AutoThreat® PRO,
stakeholders access:
- Deep and Dark Web Intelligence
- Vulnerability Intelligence
- Onboard & Offboard Threat Intelligence
- Threat Actor Engagement & Monitoring
- Upstream's Automotive Risk Matrix
- Customer-specific Risk Scoring
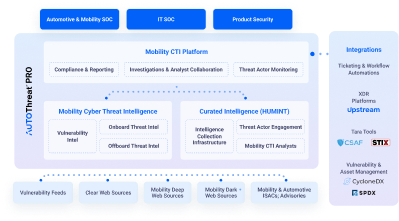
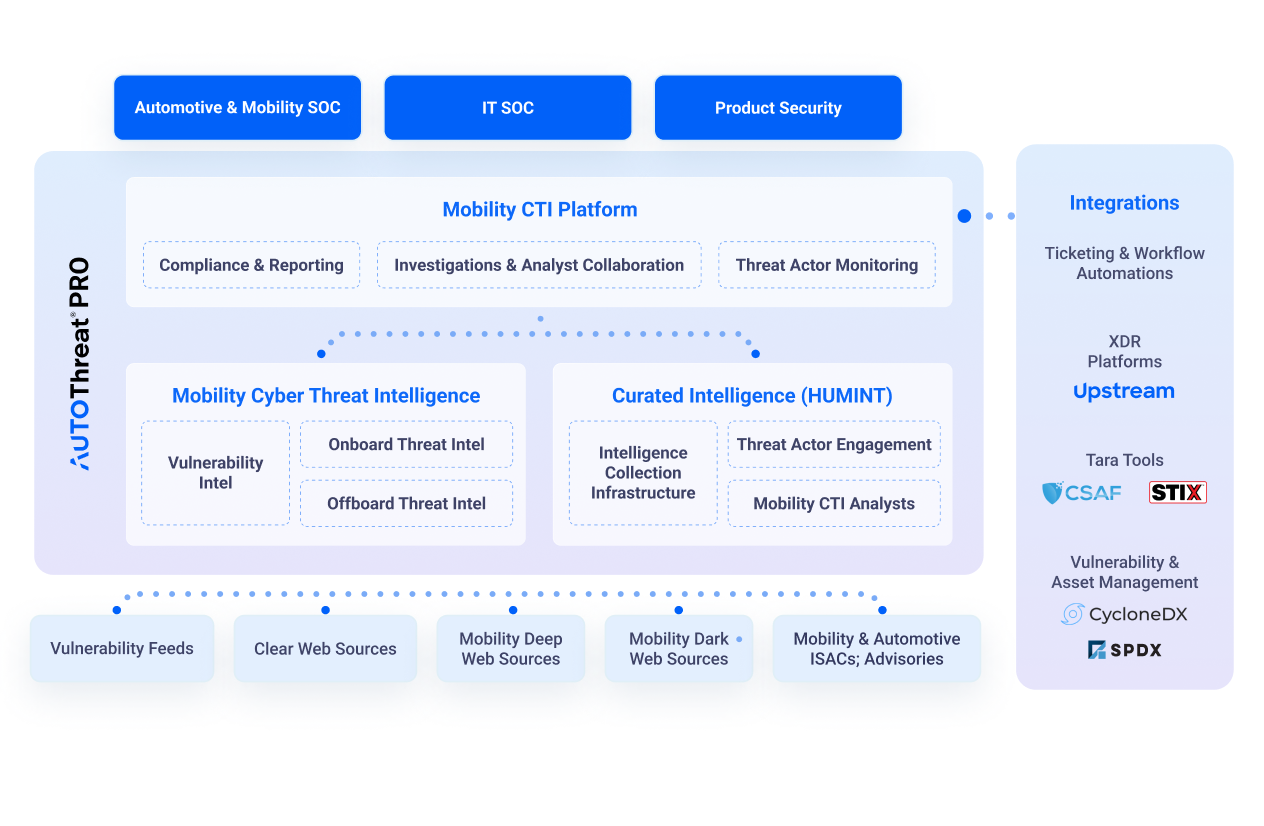
- Mobility CTI Platform
- Mobility CTI Analyst Collaboration
- Effective Investigations
- Ticketing & Automated Workflow Integration
Mobility Intelligence Fit For Your Needs
Mobility First
Mobility First
The first and only threat intelligence offering purpose-built for the automotive and mobility ecosystem, providing dedicated automotive-specific intelligence with a robust threat intelligence infrastructure for deep and dark web incident tracking, mobility vulnerabilities, threat impact analysis, and mitigation suggestions from expert analysts.
Mobility Threat Actor Repository
Mobility Threat Actor Repository
Access a proprietary repository of mobility-specific threat actors to understand the motivations, strategies, and activities facing the mobility ecosystem. This repository provides details on relevant threat actors and tactics most relevant to mobility assets and concerns, offering insights beyond generic profiles.
Onboard & Offboard Insights
Onboard & Offboard Insights
Gain insights and understand the threats facing onboard assets with findings related to in-vehicle tampering of connected products such as IVI jailbreaks or TCU rooting. Expand visibility into threats with intelligence findings on offboard assets covering external and third-party vulnerabilities, including unauthorized access to vehicle data and controls via diagnostic tools or mobile app tampering.
Proactive Engagement
Proactive Engagement
Engage directly with the mindset and tactics of threat actors through targeted investigations and insights. Gain deeper access to discussions within deep and dark web sources to better understand evolving capabilities, motivations, and tactics directly impacting mobility assets.
Map Findings to Regulations
Map Findings to Regulations
Link specific threat intelligence findings to relevant automotive, privacy, and IoT regulations, supporting risk assessment and simplifying audit preparation with demonstrated adherence to compliance requirements. Correlate insights from findings to UNECE R155 (Annex 5), MITRE, and AutoISAC’s ATM framework.
Public Automotive Cyber Incident Database
Public Automotive Cyber Incident Database
Upstream’s comprehensive cyber incident repository is constantly updated and consists of all publicly reported mobility-related incidents from clear web resources; all incidents include information on the attack type, vector, impact, geo-location, and more.
Deep and Dark Web Monitoring
Deep and Dark Web Monitoring
In addition to collecting automotive-related cyber incidents reported publicly, AutoThreat® PRO also monitors deep and dark web sources to detect early signs of intended exploits and track incidents found throughout private forums, marketplaces, and social network channels.
Stand-Alone or API
Stand-Alone or API
AutoThreat®PRO intelligence can be accessed using the Cyber Threat Intelligence platform, where stakeholders can effectively investigate findings, track their status, and drill down into the details. Threat intelligence can also be integrated into ticketing and automated workflows in vSOC, PSOC, PSIRT, and more due to its STIX formatting and API capabilities.
Ready for the latest insights from our analysis of automotive cyber incidents?
Subscribe now