Upstream’s Stateful
API Security
AI-powered and contextual approach to detection, investigation, and response of a wide range of cyber and operational API threats.
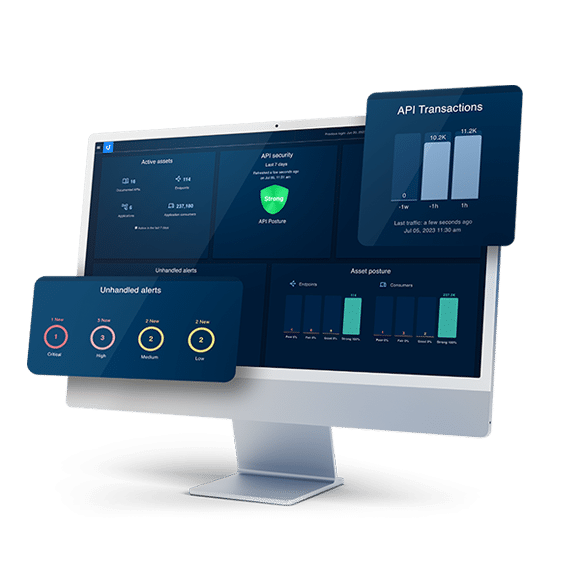
Using the power of the proprietary live digital twin
to deliver the most extensive API Security coverage
Expand coverage well beyond OWASP API Security Top 10
with purpose-built deep contextual and operational analysis of API traffic
Built for Massive Scale and Complex Enterprise Environments
Process billions of monthly API transactions. Flexible SaaS or customer cloud deployments to meet PII and regulatory requirements. The platform offers deep integrations with cloud infrastructure and data lakes to ensure smooth data ingestion and offer cross-organizational visibility into operational and cyber threats.
Customized Cyber, Business Logic, and Operational Risk Detection
The live digital twin extracts contextual information from API traffic to build a stateful analysis of endpoint and consumer behavior. The result is extended threat detection coverage, including cyber risks, data exposures, operational risks and API misuse.
Robust AI Capabilities for Effective Threat Detection and Large-Scale Investigations
Upstream’s Ocean AI offers purpose-built ML, GenAI and Agentic AI capabilities including ML-powered detection to cover low-and-slow and complex attacks, as well as unknown risks. GenAI tools offer cyber teams the ability to easily query data for investigations and threat hunting. Agentic AI tools offer advanced detection authoring for rapid detection.
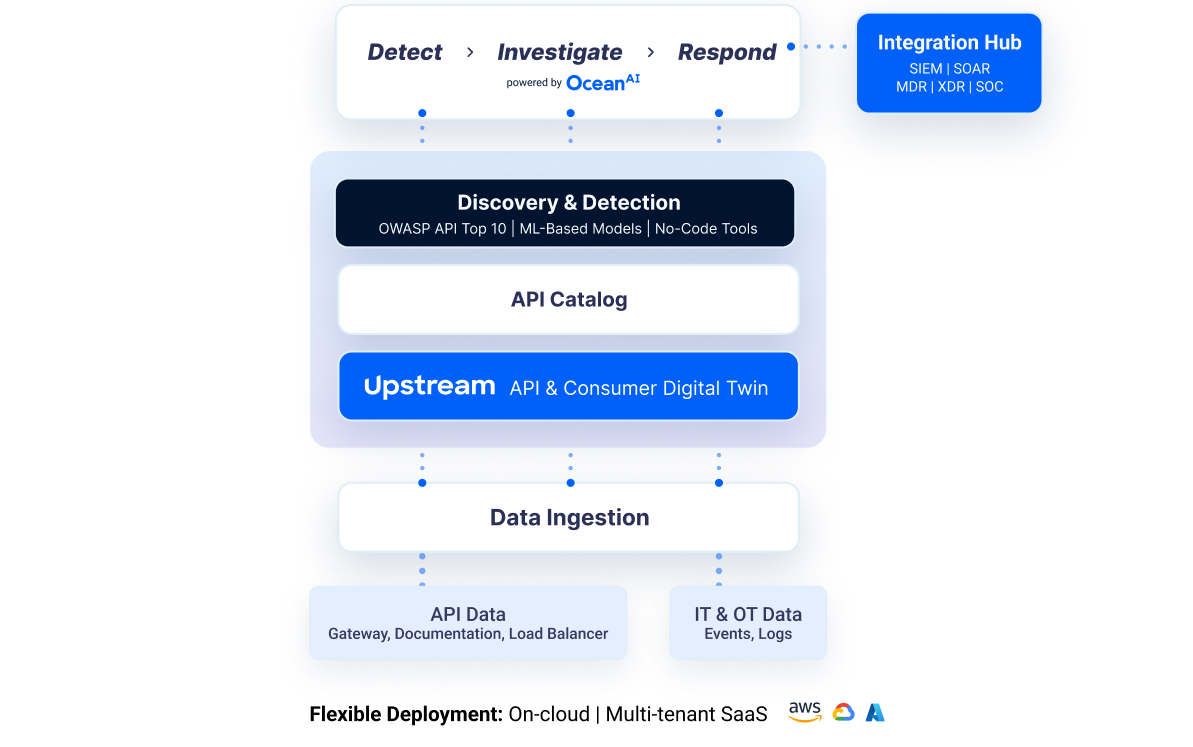
Automated discovery and catalog
Identify, classify, and understand all API endpoints and consumers.
Upstream constructs a comprehensive API inventory by ingesting API traffic, API documentation (if available), and operational logs to uncover all active endpoints, including undocumented, shadow, and zombie APIs. Through automated endpoint and parameter learning, AI powered data classification, and structural analysis, the platform builds a continuously updated catalog that describes each API’s purpose, data exposure, and functional relationships. This foundational visibility defines what exists, how it is used, and where sensitive or high-risk surfaces reside.
ML-based detection
Apply stateful, ML-driven behavioral context to surface known and unknown threats.
Using the live digital twin and Ocean AI, Upstream applies stateful, ML-driven behavioral analysis to detect anomalies and attack patterns. By correlating API transactions with inferred behavioral baselines for endpoints, parameters, and consumers, the platform evaluates request, response, and authentication behavior over time and identifies deviations, misuse, or sequential activity indicative of distributed or low-and-slow attack chains. Coverage includes OWASP Top 10, misconfigurations, business-logic abuse, enumeration, and fraud attempts, with additional flexibility provided through a no-code detection builder for customer-specific logic.
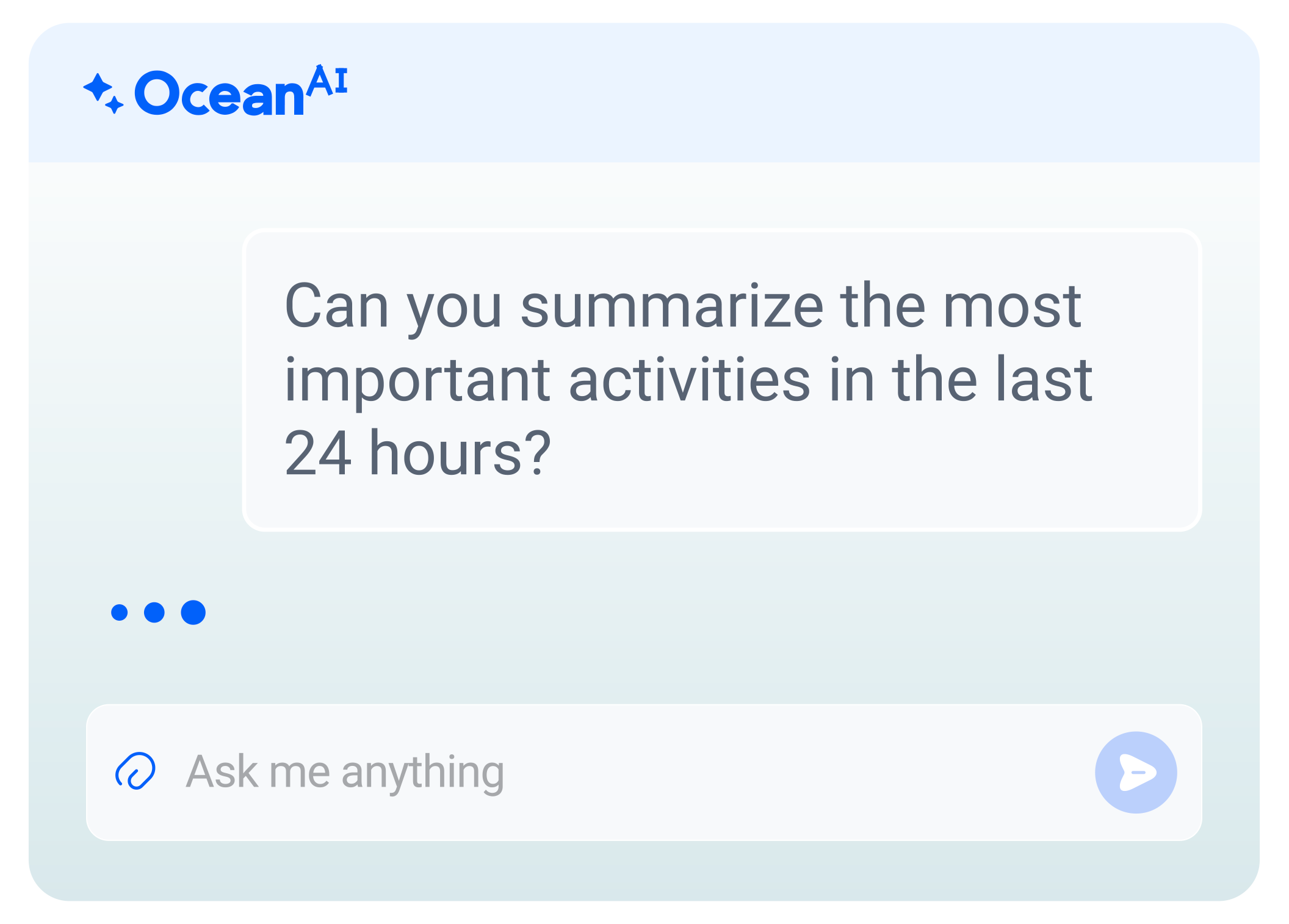
GenAI-powered investigations and threat hunting
Reconstruct events and understand impact with contextual correlation with natural language querying.
Upstream provides full transaction history and cross-entity correlation, allowing analysts to trace how events unfolded across APIs, sessions, and consumers. Behavioral baselines, endpoint profiles, historical deviations, and related operational signals are used to reconstruct event chains, validate anomalies and proactively executive threat hunting. Ocean AI supports investigations with GenAI-driven summaries, data classification, alert interpretation, and querying, helping teams determine scope, impact and remediation options quickly.
Effective response and Agentic AI tools
Coordinate remediation through integrated workflows and automated actions.
Upstream connects with SIEM, SOAR, WAFs, API gateways, and other enterprise systems to support automated or analyst-driven remediation. Actions can include blocking or isolating API consumers, revoking tokens, adjusting rate limits or policies, and sending enriched alerts to external systems.
API Security Frequently Asked Questions
A typical WAF is stateless and examines transactions one by one. Upstream uses proprietary live digital twin technology to build a stateful, contextual analysis of endpoint and consumer behavior. This allows the platform to detect complex, low and slow attack chains that look like legitimate traffic to a standard WAF.
Foundational visibility is the core of our platform. Upstream automatically constructs a comprehensive API inventory by ingesting traffic, documentation, and operational logs. This process uncovers all active endpoints, including undocumented, shadow, and zombie APIs. It continuously updates the catalog to classify data exposure and functional relationships.
Yes. Beyond standard OWASP Top 10 coverage, the platform includes a no-code detector builder. This allows your team to create tailor-made detectors for unique business logic, fraud attempts, or operational risks without writing a single line of code. You can leverage your own signals and historical data to stop misuse specific to your ecosystem.
No. Upstream is designed as a cloud-native solution with a zero latency impact. The platform typically ingests data via traffic mirroring from your gateway, load balancer, or a lightweight agent. This ensures your critical applications remain fast and responsive while under full security monitoring.
Ocean AI offers purpose-built GenAI and Agentic AI tools to streamline investigations. Analysts can use natural language querying to reconstruct event chains and understand the root cause of an anomaly quickly. It provides GenAI-driven summaries and alert interpretations, helping your team determine the scope and impact of threats at scale.
We offer flexible deployment to meet your specific regulatory and PII requirements. You can choose a multi-tenant SaaS model or deploy directly within your own private cloud environment. The architecture is built for massive scale and can process billions of monthly API transactions across various infrastructures.
More to dig into on API Security
Impact of PCI DSS on API Security For Mobility Products, Apps, and Services
Read more

Beyond the Cyber Resilience Act: Building Holistic Cyber Resilience
Read more
Upstream’s Ocean AI Dramatically Improves API Security Investigations
Read more
Upstream Safeguards Autonomous Vehicle Technology with May Mobility
Read more
Ford Trucks Collaborates with Upstream Security to Protect Its Connected Vehicles Against Cybersecurity Risks
Read more
Fifty Robotaxis, One Dead End: A Real-World Stress Test for Mobility API Resilience
Read more
APIs in the Driver’s Seat: AI Agents and the Future of Automotive Cybersecurity
Read more
