

Warning: This car may contain vulnerable Software or Hardware
In many industries, there is growing demand for transparency in product processes and content. Companies are increasingly asked to detail the composition of their products and where they have been made. Consumers are now aware if their sneakers were made in sweatshops or if their food contains animal products. In turn, many companies have to invest heavily into finding alternatives to attract and retain their customers.
However, when it comes to consumer electronics or the automotive industry, transparency is not always readily available. For example, consumer electronics companies and automotive OEMs may struggle to provide transparency either due to a logistical challenge (it is quite challenging to produce and manage a bill of materials for a product consisting of hundreds of thousands of parts, such as a car), or it is kept secret, as the product’s components and processes are seen as core competitive advantages where the producer or supplier simply does not want to provide the information.
As such, a connected car could contain vulnerable hardware or software, and the consumer, whether that be the driver, or the OEM purchasing the components from a Tier-1 or 2 supplier, could not know the danger. Even if a consumer did want details of the vehicle components, tracking them would be a daunting task. Consumers simply have to trust the suppliers, car manufacturers, or regulatory bodies with issues that directly relate to their health and well-being. Often, OEMs and federal bodies do not even have access to the in-depth component data and potential threats posed by them.
The Supply Chain Black-Hole
These concerns are inextricably related to one of the most significant challenges facing the automotive industry today – the supply chain.
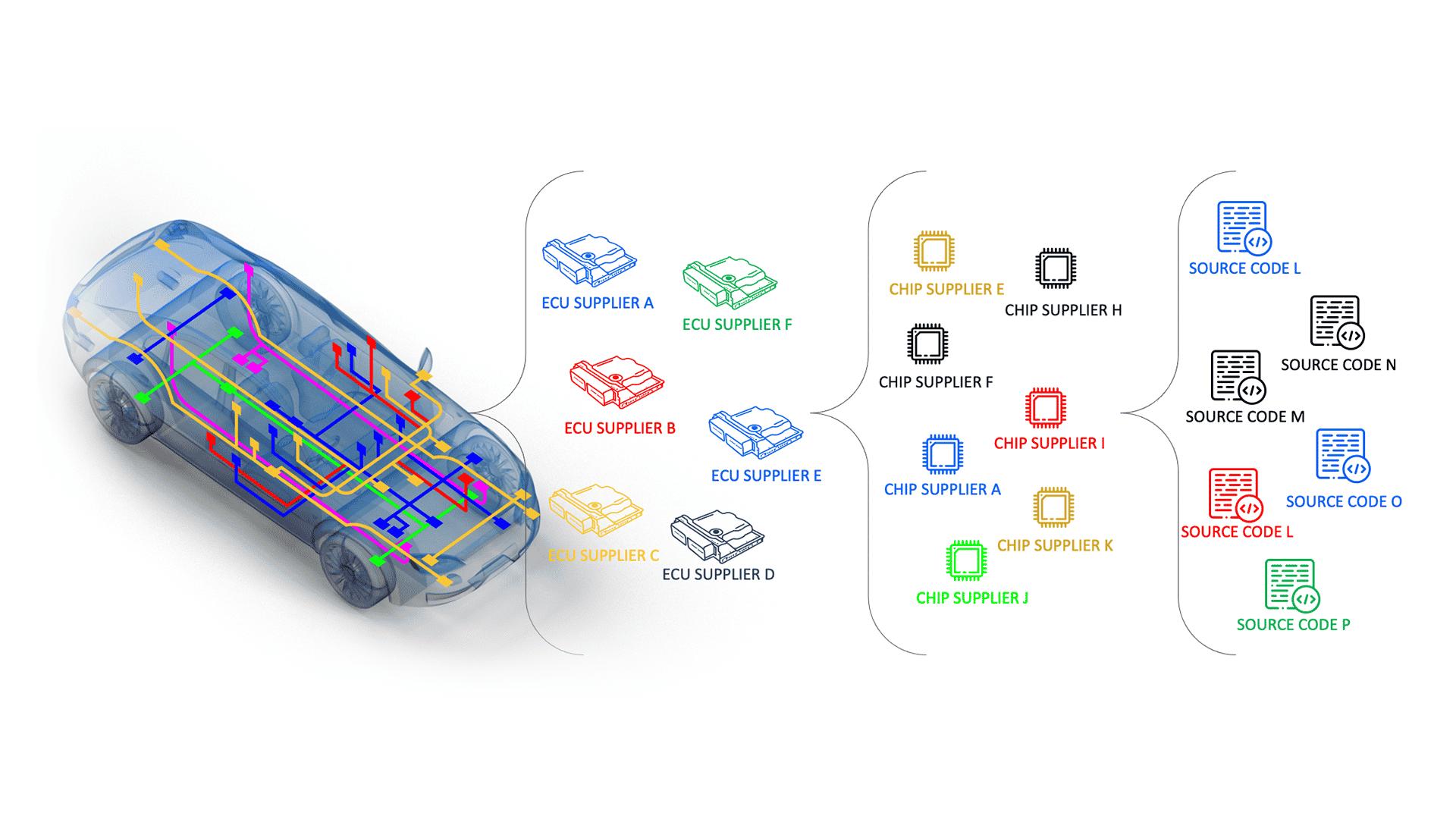
Simply put, the OEM who builds the vehicle assembles it from thousands of software and hardware modules and systems produced by Tier 1 suppliers. These thousands of components are constructed from various individual components supplied to the Tier 1s by their Tier 2s. And so the cycle goes on. Each component’s quality and safety are entrusted to the company that produces it.
But who is overseeing the quality and safety of each company in the supply chain? The supplier producing the components could easily vary its sources according to its agenda, safety standards, or financial capability. This can lead to a scenario where an OEM and drivers are left in the dark of what is under the vehicle’s hood.
This isn’t a theoretical issue. It is happening right now.
In early 2021, a security researcher hacked the lcn2kai Bosch infotainment unit in a Nissan Xterra vehicle. The hacker found a vulnerability in the infotainment system; by plugging in a USB device, they could gain root shell access to the system and gain administrator access to install unauthorized software. The hacker added that Bosch’s infotainment vulnerability could also affect additional Nissan models produced after 2015, including Rogue, Sentra, Altima, Frontier, and various other commercial models.
Upstream research then revealed that additional OEMs installed a similar Bosch infotainment in various car models, which may expose them to the same vulnerability. This begs the question, what other models or companies are impacted by this component vulnerability? Would the driver of said vehicles even know they had a vulnerable component installed in their car?
Upstream research then revealed that additional OEMs installed a similar Bosch infotainment in various car models, which may expose them to the same vulnerability. This begs the question, what other models or companies are impacted by this component vulnerability? Would the driver of said vehicles even know they had a vulnerable component installed in their car?
Not every OEM tracks potential cyber vulnerabilities related to the components. Therefore there is no guarantee that the Tier 1 supplier responsible for the vulnerability replaced the model and addressed the vulnerability in tens of thousands of vehicles.
The OEM challenge of tracking and effectively addressing component vulnerabilities grows even more significant due to the global shortage of semiconductors. Due to increasing demand and subsequent shortage of components, Tier 1 suppliers may attempt to secure new Tier 2 components more hastily, without allowing the proper time for due diligence to ensure its origins and potential vulnerabilities.
Navigating through the supply chain black hole
The growing challenge of managing the automotive supply chain and its potential cybersecurity impact led international regulators and standardization bodies to address it in recent regulations and standards. The UNECE WP.29 R155 CSMS regulation and the ISO/SAE 21434 standard both call for management of the automotive supply chain.
The WP.29 R155 regulation indicates that the onus of supply chain cybersecurity management lies upon the OEM, where it is the vehicle manufacturer’s responsibility to ensure that all vehicle components and parts, both hardware and software, are secure.
The WP.29 R155 also clearly demands (in Section 5.1.1) that the OEM must “collect and verify the information required under this Regulation through the supply chain so as to demonstrate that supplier-related risks are identified and are managed.”
The ISO/SAE 21434 standard also highlights the importance of supply chain management. Clause 15 of the standard focuses on “distributed cybersecurity activities” and discusses the cybersecurity relationship between OEMs and Tier 1 and 2 suppliers.
The standard indicates that an OEM is responsible for ensuring that the suppliers used are implementing methods to ensure their products and components are cyber secure and recommends the implementation of three main strategies to develop a successful supplier and OEM relationship:
- Evaluate: (Clause 15.4.1) “Demonstration and Evaluation of Supplier Capability”
- Confirm: (Clause 15.4.2) “Request for Quotation”
- Align: (Clause 15.4.3) “Alignment of Responsibilities”
Upstream AutoThreat® Intelligence fills in the missing link
Upstream’s AutoThreat®, an automotive-specific cyber threat intelligence service, aids OEM’s, Tier 1s, Tier 2s, insurance companies, and other related organizations to cope with the supply chain management challenge and comply with essential aspects of the regulations and standards.
Upstream’s AutoThreat® research team leverages intelligence from multiple internal and external sources to analyze vulnerabilities, automotive-oriented cyberattacks, and threats, as well as develop countermeasures to protect Upstream’s customers. Upstream uses various threat analysis tools to capture various threat indicators from public feeds and deep and dark web activity.
Vulnerabilities in automotive components and vehicles are uncovered and combined with threat metadata gleaned from connected vehicle data feeds. Threats are then analyzed and assessed in light of a growing library of automotive components to distill potential impacts across a variety of vehicle models.
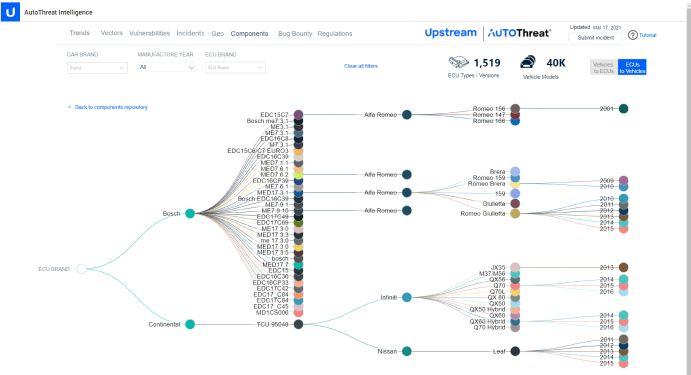
AutoThreat® includes a designated section dedicated to detecting vehicle component and device vulnerabilities by documenting vulnerabilities at the vehicle, component, and infrastructure level and offering ECU and vulnerability mapping correlated to individual vehicle models.
Upstream’s threat analysts are constantly updating the sources to increase coverage and include additional suppliers and OEMs to enable its users to understand what threats relate to their vehicle and help organizations develop their own intelligence-led security operations with the unique nuances and understanding required of moving vehicle infrastructures.


