
With new cybersecurity regulations and standards coming into effect, such as UNECE WP.29 R155 & R156 and ISO/SAE 21434, automotive OEMs are feeling pressure from multiple angles to reimagine their cybersecurity posture.
Ever-complicated supply chains, growing vectors, and increased hacker sophistication are just some of what needs to be considered for any cybersecurity measure to be effective.
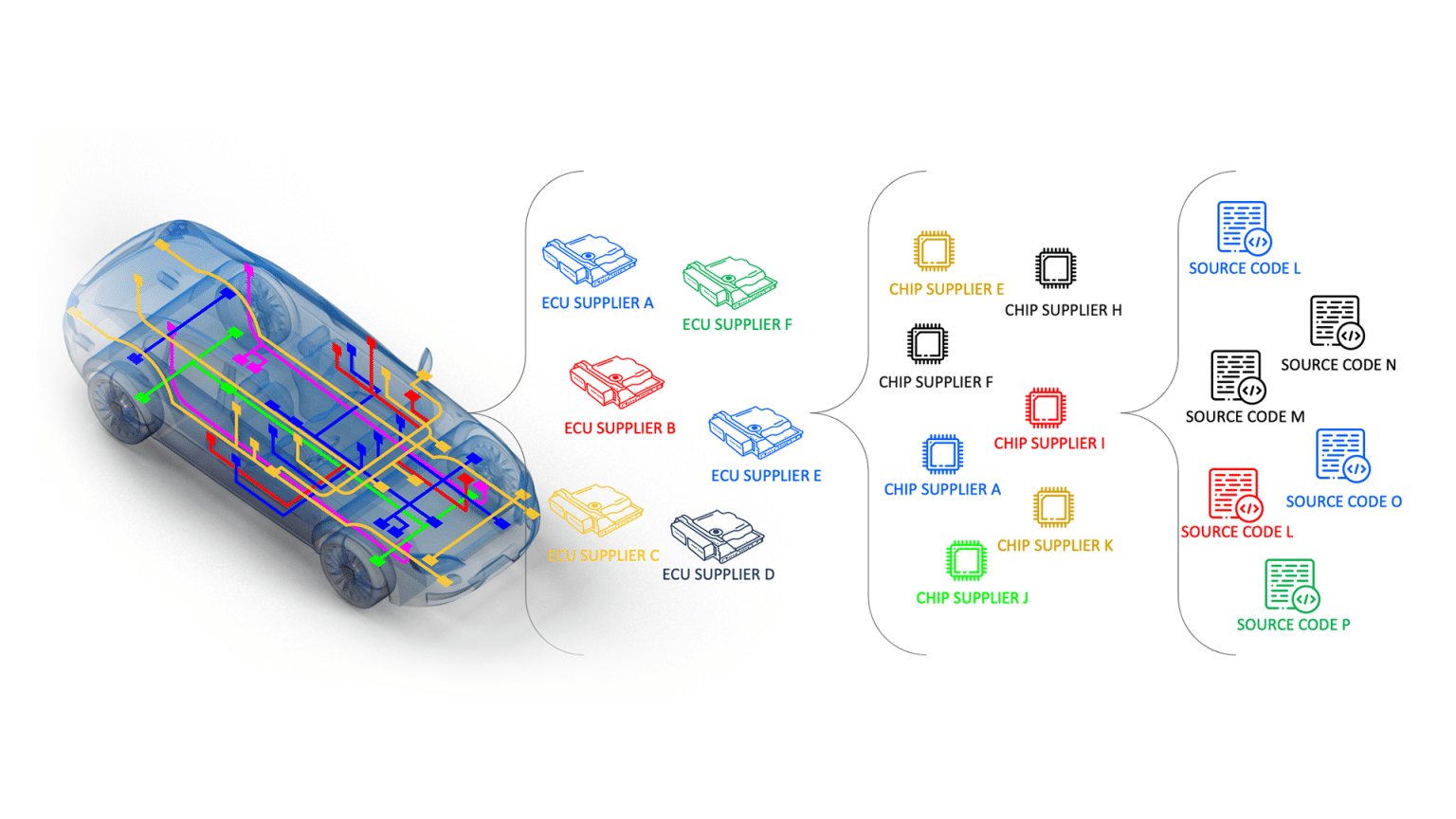
Monitoring the automotive supply chain is key
Potential risks to the automotive industry exist in multiple layers, presenting the opportunity to strike a wide variety of vehicles from a single weakness. This is seen when a vulnerability is discovered on a Tier-1 or Tier-2 component by a Black-hat actor. A quick search can find that one of these components is used by multiple OEMs, presenting a prime opportunity for hackers to strike.
This is seen in new risks and attacks against the automotive industry on a near daily basis. For Example, our AutoThreat® Intelligence analysts reviewed an incident published by Tencent Security, who discovered numerous vulnerabilities in a European OEM infotainment system. The researchers carried out a detailed study of the system and found many security flaws triggering vehicle hacking attacks and shared their findings in a detailed white paper. The researchers found multiple attack surfaces including in a JavaScript engine, Bluetooth stack, Wi-Fi chip, USB functions, and third-party head unit apps that utilize the infotainment ECU in vehicles as far back as 2018.
Potential attack paths
Connected vehicles have two major entry points that are considered as possible attack paths for a hacker to gain illicit access to the vehicle. First is the Telematics module, also known as TCU, T-box, and assorted unique names per automotive OEM. This modem-like device is in charge of two-way communication between the vehicle and the OEM’s backend servers, referred to as the “automotive cloud”.
The second is the head unit, sometimes called the infotainment, In-Vehicle Infotainment (IVI), or multimedia system. This system controls multiple functions such as navigation, video, and mobile connectivity, using a screen-based interface. Head unit software often runs on common operating systems like Windows, Linux, or QNX, and are used by multiple OEM’s, with some moving towards a shared Automotive Grade Linux-based systems.
The importance up-to-date software
The OEM head unit consists of several boards and a TCU. Each has a unique IP address, which communicates with one another via designated ports. The relevant board that poses cybersecurity concerns by Tencent research is called the “Country Specific Board” (CSB) by the OEM. The CSB runs a Jacinto 5 Linux system and contains chips from NXP and u-blox.
By disconnecting the CSB and connecting a testing computer to the head unit instead, the researchers managed to trick the head unit into thinking the computer is the CSB, merely by emulating the CSB’s static IP address. This action granted the researchers root access to the head unit, allowing for them to disable anti-theft mode, take over the head unit’s display screen, and execute other commands.
The attack was successful due to several factors, such as an out-of-date Linux kernel version with several known vulnerabilities. The head unit runs on an old Linux kernel version (3.18.71) which includes known vulnerabilities as privilege escalation (CVE-2017-6001).
Besides exploiting the four year old CVE mentioned above, five new CVE’s were uncovered by the Tencent Security research team within several additional units.
The right environment for a cyber-attack
As we just saw, vehicles today consist not only of mechanical components but also of connectivity and software code, making them “computers on wheels”.
Being connected to the internet offers valuable capabilities while also exposing them to cyber threats. In most cases, these parts do not contain only OEM-made components but Tier-1 and Tier-2 parts.
Multiple companies partaking in the building and installation of a single component opens opportunities for hackers to conduct a single attack that can have a long-lasting impact on thousands of vehicles. These are the exact attacks that UNECE R155 & R156 as well as ISO/SAE 21434 aim to prevent and address.
To prevent these attacks from ever taking place, Upstream’s AutoThreat® Intelligence monitors OEM, Tier-1, and Tier-2 components on the clear, deep, and dark web with the purpose of uncovering new vulnerabilities. These include fully disclosed vulnerabilities, newly discovered exploits, and even specialized forums that collude to crack a piece of software. In each of these scenarios, once uncovered, the Upstream’s AutoThreat® analyst team immediately notifies its relevant customers and also provides recommendations for taking actions and mitigating the risk, protecting assets from any threat.
Beyond meeting regulatory requirements, this best-in-class automotive intelligence service works to keep assets and automotive servers secured.
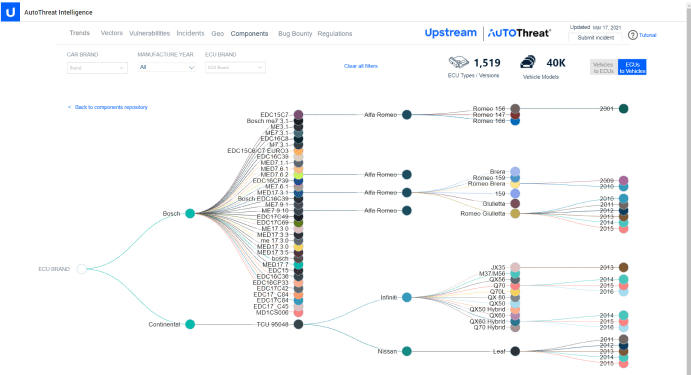
Upstream’s AutoThreat®: Security vulnerabilities mapped to vehicles models and components
Upstream’s automotive-specific analysts collect vulnerabilities exposed in the clear, deep, and dark web. They are analyzed and documented by the team to strengthen AutoThreat® and better protect customers. Upstream’s analysts also maintain a mapping of components, their embedded chipsets, operating systems, and the vehicle models they are deployed in.
Once a new vulnerability is exposed, such as in a Wi-Fi chipset, it is immediately mapped to different components across vehicle makes, models, and years. This allows Upstream to identify vector threats for our customers before hackers do.
A single vulnerability in a chipset can impact hundreds of thousands of vehicle models from multiple OEMs. Upstream AutoThreat® can help OEMs, Tier-1, and Tier-2 suppliers gain immediate visibility to their complex supply chain risks, allowing them to identify and respond rapidly.
AutoThreat® component mapping dashboard
As part of Upstream’s AutoThreat® Pro services, whenever a new vulnerability is detected in any part of the supply chain, subscribers are immediately alerted with a full report of the risk and mitigation recommendations.
With AutoThreat®, OEMs, Tier-1s, and Tier-2 suppliers can rely on seasoned automotive analysts to constantly monitor cyber risk that may be hidden throughout the supply chain. True data-driven insights allow them to respond rapidly to threats and comply with automotive cyber security standards and regulations like never before.
The above incidents are just some examples out of many other similar incidents published in recent years related to vulnerabilities within vehicles’ components.
One of Upstream’s AutoThreat® Intelligence key benefits is to help OEMs, Tier-1, and Tier-2 suppliers evaluate potential cyber security risks regarding connected vehicles and their components, mitigate or prevent them, and comply with standards and regulations.
To take a deeper dive into what’s happening in the field and how to strengthen your cybersecurity posture, download our 2022 Global Automotive Cybersecurity Report.