Cybersecurity Detection & Response Platform
Secure connected vehicles and IoT devices against cyber threats and attacks with a multi-layered detection and response platform, purpose built for the Automotive and Smart Mobility ecosystem.
Request a Demo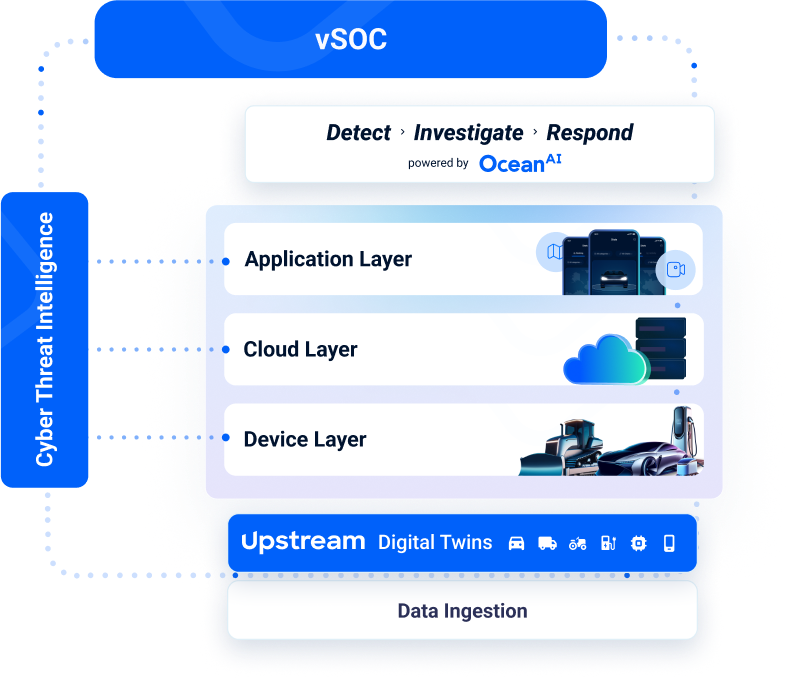
A Holistic Approach to Securing Connected Vehicles and IoT Devices
Upstream helps OEMs, suppliers, and Smart Mobility stakeholders secure their assets,
comply with regulations, and identify new business opportunities by unlocking the value in mobility data.
Monitor & Detect
Upstream offers a comprehensive XDR solution for automotive and IoT cybersecurity, leveraging near-real-time monitoring and ML-based anomaly detection for threat mitigation.
Respond
Upstream enables prompt and effective threat mitigation and SOC optimizations with Generative AI-powered investigations, automated remediation and response, leveraging domain expertise in automotive cybersecurity and field-proven playbooks.
Comply
Upstream assists OEMs and mobility stakeholders in meeting cybersecurity standards and regulations, including the UNECE WP.29 CSMC regulation R155 and the ISO/SAE 21434 standard.
-
Agentless and Cloud-Based
The Upstream XDR platform is agentless, requiring no software or hardware installations in vehicles or IoT devices. Its cloud-based architecture allows for rapid deployment, delivering near real-time monitoring and detection of cyber risks.
-
ML-Based Detection Models
Upstream’s comprehensive detection capabilities can identify both known and unknown cyber threats. By leveraging advanced purpose-built machine learning models that correlate data from multiple connected vehicle and mobility sources, the platform ensures protection for individual assets and entire fleets, while providing detailed insights into anomalies.
-
AI-Powered Investigations
The Upstream Platform leverages Ocean AI, an integral advanced AI layer, enabling cybersecurity analysts and SOC teams to investigate cyber risks and extract insights through a simple conversational interface. With these newly introduced GenAI capabilities, cyber teams can optimize alert filtering, handling, and prioritization; they can make smarter, more informed decisions, identify patterns and trends and ultimately accelerate time-to-response.
-
No-Code Customization
Upstream’s solution includes a robust set of pre-built detectors that cover a wide range of cybersecurity use cases and accelerate security responses. It also allows for customization of detectors and the creation of user-defined detectors using its no-code capabilities, enhancing adaptability and coverage.
-
Prompt Threat Mitigation
The system automatically triggers workflows and playbooks on third-party platforms, with each alert detailing the affected asset’s digital twin data. Configurable to meet various requirements, Upstream seamlessly integrates automotive cybersecurity insights into other systems, such as SIEM, SOAR, or workflow automation systems, as well as into vSOC operations
-
Regulatory Compliance
Upstream ensures compliance with current cybersecurity, data privacy, and mobility safety regulations. The platform’s monitoring and detection capabilities meet the UNECE WP.29 R155 requirements for a cybersecurity management system (CSMS) and are in line with NHTSA’s crash reporting guidelines. It also supports compliance with the ISO/SAE 21434 standard and includes options for data anonymization, PII stripping, obfuscation, and encryption to address GDPR data privacy mandates.
Upstream delivers a multi-layered cybersecurity detection and response platform , purpose-built for the mobility and transportation ecosystem. This comprehensive approach ensures proactive threat analysis, robust detection and response, coupled with effective monitoring and remediation.

Cyber Threat Intelligence
Leverage cyber threat intelligence to proactively expand your understanding of cyber threats and risks. Adopt an intelligence-led strategy with thorough monitoring of the deep and dark web for effective cyber threat mitigation. Access mobility-specific and component-based intelligence as well as detailed threat actor mapping.
Learn moreCybersecurity for the Expanding
Smart Mobility Ecosystem
Don’t wait until it’s too late. Secure your mobility assets today.
Learn more about how Upstream can help secure everything that moves by requesting a demo.

